Index
- What are the different types of malware ?
- What are the means of propagation used to send you a malware ?
- How does an antivirus work ?
- The cyber-attacks that have marked history
- Some protective measures to take and how to detect an infection
What are the different types of malware ?
A malware is a program developed for the purpose of harming a computer system, without the consent of the user whose computer is infected.
Here are the most common types of malware:
Virus
Just like the flu virus, a computer virus is designed to spread from one host to another, with the ability to replicate. Like a virus that can not reproduce without a host cell, the computer virus can not proliferate without a program, such as a file or document.In more technical terms, a computer virus is a type of code or malicious program that aims to change the operation of a computer and to spread from one machine to another.
The computer virus is embedded in a program or attached to a legitimate document that supports macros in order to execute its code.
This can cause unexpected effects or damage: for example, it will damage system software by altering or destroying data.
Once a virus successfully joins a program, file, or document, it remains inactive until special circumstances cause its code to run on the computer or device.
In order for a virus to infect your computer, you must launch the infected program, which in turn triggers the virus code.
Worms
Unlike viruses, worms do not require human intervention to spread and infect computers: this is a program that can use computer networks to infect other connected machines without the help of users .The worm is often transmitted to computers in different ways, such as email, obscure source programs, forum sites, DVDs and pirated game CDs ..
Trojan Horse
Trojans are called this way because they act like the Trojan horse of Greek mythology, pretending to be legitimate programs while carrying out malicious operations.The main Trojan horses are programs opening ports of the machine, that is to say, allowing its designer to enter your machine through the network by opening a backdoor.
Since the user is generally unaware that he has installed a Trojan horse, the security of the computer device depends on the ability of its antivirus to recognize the malicious code, isolate it and delete it.
Backdoor
A backdoor, also known as Remote Administration Tool (RAT), is an application that allows certain users (system administrators or cybercriminals) to access the system of a computer without the user authorizing it or not know.Depending on the RAT feature, the hacker can install and launch other software, send keyboard commands, download or delete files, turn on your microphone or camera, and record your computer's activity to communicate to the hacker.
Rootkit
A rootkit is a very complex malware that gets attached to the core of an operating system(Windows - Linux), which is why it is very difficult to detect and remove.A Rootkit has two characteristics:
- Changing the operation of an operating system.
- The possibility of becoming almost undetectable.
But it can also hide other parasitessuch as spyware, trojan or serve as a client to bot networks.
Other technical means may hide a Rootkit, for example the protection systems of Audio CDs.
Once the Rootkit is active, it becomes the master of the system, even anti-virus programs and other protection software will be unable to act effectively.
Spyware
Spyware acts as its name suggests, spying what you do on your computer It collects data such as keylogger entries, browsing habits, and login information that are sent to third parties, typically cybercriminals.It may also change specific security settings on your computer or interfere with network connections.
Adware
Adware is one of the most common nuisances encountered online. Programs automatically send advertisements to host computers.Common types of adware programs include contextual advertisements on web pages and in-program advertisements that often accompany free software.
While some adware is relatively safe, other variations use tracking tools to retrieve information about your site or browsing history and display targeted ads on your screen.
Ransomware
Ransomware infect your computer, then encrypt sensitive data such as personal documents or photos, and then ask for a ransom to recover them.If you refuse to pay, the data is deleted.
Some variants of ransomware lock access to your computer. They can claim to come from legitimate law enforcement agencies and suggest that you have been caught for doing something wrong.
Robots
Robots are programs designed to automatically execute specific operations. They are used for many legal purposes but have been redefined as a type of malware.Once in the computer, the robots can cause the machine to execute specific commands without the user authorizing or being informed.
Hackers may also attempt to infect multiple computers with the same bot to create a "botnet", which can then be used to remotely manage infected computers for the purpose of stealing sensitive data, spying on the victim's activities. , automatically distribute spam or launch devastating DDoS attacks on computer networks, websites ...
What are the means of propagation used to send you a malware ?

I will show you the means of propagation that are most often used to send you a malware, but know that behind all this, there is often SOCIAL ENGINEERING, which has a fully dedicated article on my blog HERE
The main means of propagation are:
- Visit an infected website
- Connecting a device to your computer (usb key, hard drive ...)
- Mail: attachments, links
- Social networks: attachments, links
- Public wifi networks
- Systems with known vulnerabilities that have not been updated
How does an antivirus work ?

Antivirus is software designed to identify, neutralize and eliminate malware.
I will explain quickly without going into details, how an antivirus works.
There are several methods an antivirus uses to detect malware:
Signature Detection
It is also called scan. This is the oldest and most used method.
This method consists in analyzing the hard disk, looking for the signature of the virus, which is present in the database of the software, if it is up to date and knows this virus.
The signature is a piece of code or a string of the virus that identifies it. Each virus has its own signature, which must be known to the antivirus.
This method is not effective against new viruses or so-called polymorphic viruses, whose signature changes with each replication.
The advantage of the scan technique is that it can
detect viruses before they run in memory
To remain effective, the antivirus must regularly update its antivirus database. A monthly update frequency is an acceptable minimum.
The integrity check
Checking the integrity of a file consists of checking that it has not been modified or altered over time.
The antivirus, to check the integrity of the files, will store a central file listing all the files on the disk with which it has associated information that may change when the file is changed:
- Size
- Date and time of last modification
- The checksum (CRC: cyclic redundancy code)
If an anomaly arises, the user is informed. To partially counter this parry, viruses do not necessarily change the file modification date, or restore it.
Heuristic analysis
Antivirus usually includes a heuristic analysis function. This heuristic treatment consists of an analysis of suspicious codes via the search for instructions usually used by the viruses.
The goal is to detect viruses that are not yet known antivirus vendors.
The heuristic scanner looks for unusual calls or instructions to the system, network applications, or email clients. When the number of these normally exceptional behaviors exceeds a certain threshold, the scanner emits an alarm.
How does the antivirus react ?
The antivirus continually monitors the behavior of active software (if it is running and automatic protection is enabled). It scans all modified and created files. In case of anomaly, it warns the user by an explicit message
When the antivirus detects a virus, it offers three possibilities to the user:
- Repair file: The antivirus must be able to repair an affected file. But that's not always possible.
- Delete file: If the antivirus is not able to delete the file, you can delete it.
- Quarantining the infected file: This is a wait solution. The antivirus places the file in a safe folder on the hard drive. When the antivirus will be able to repair the file, you will be able to extract the file from the file and fix it.
The cyber-attacks that have marked history
In this part, I will give you a summary of the biggest cyber-attacks known to date, without going into the technical details, but simply so that you know about it because I think it's important to know the history cyber attacks, to understand the current ones.
I would like to point out that I did not fully regulate this part, you may find identical phrases on the Wikipedia pages, because they were very well constructed and explanatory.
Here is a list that presents the computer attacks that have marked the whole world:
Stuxnet
Stuxnet is considered as the most ingenious cyber attack and the one that has revolutionized the world of computer security.
Stuxnet is discovered in June 2010, but studies will show later that his career probably began a few years earlier, in 2005 or 2006, about the same time Tehran got the wrath of some of the international community by announcing the resumption of its work around uranium enrichment.
We still do not know who created it and why, however, a rumor wants it to be an invention of the US and Israeli secret services in order to sabotage the Iranian nuclear program. This hypothesis is quite likely: this malware has indeed made the centrifuges used to enrich uranium inoperable, which has delayed the Iranian nuclear program by several years.
In general, malwares relies on the exploitation of one or two security flaws that have already been documented and even corrected. Sometimes, the virus exploits a new vulnerability: it is called zero-day, whose large-scale exploitation is an event. Stuxnet exploits four 0-day vulnerabilities affecting Windows environments.
This is the first discovered worm that spies and reprograms industrial systems, which carries a high risk. It specifically targets SCADA systems used for the control of industrial processes.
Stuxnet has the ability to reprogram Siemens Programmable Logic Controllers (PLCs) and hide its modifications.
The creators of Stuxnet managed to infect disconnected and protected devices, which caused a wave of panic. Then, according to several experts, they lost control of the worm that began to spread actively, but without causing visible damage to home or business computers, since it was originally created to attack precise industrial systems.
The worm has affected 45,000 computer systems, including 30,000 located in Iran, including PCs owned by employees of the Bouchehr nuclear power plant. The other 15,000 computer systems are computers and power plants in Germany, France, India and Indonesia, Siemens technology users.
To learn more about this attack, I advise you to watch the documentary entitled 0-day, which traces the whole history of this attack and its process.
WannaCry

Wannacry (also known as WannaCrypt), is a malware ransomware (see the beginning of this article for more information on this type of malware) self-replicating.
This cyber attack is considered the biggest ransom piracy in the history of the Internet. He encrypted the disks of a computer and asked for a ransom of $ 300 to $ 600 in bitcoin to decrypt the computer.
In May 2017, it was used in a massive global cyberattack affecting more than 300,000 computers in more than 150 countries, mainly in India, the United States, and Russia, using the outdated Windows XP system and more generally versions prior to Windows 10 (mainly Windows 7) that did not perform the security updates, in particular that of March 14, 2017.
Vulnerabilities obviously exploited by the NSA, since they served as a base for various tools of US agency spies unveiled by the Shadow Brokers, a group of pirates.
Among the most important organizations affected by this attack are Vodafone, FedEx, Renault, Telefónica, the National Health Service, the Liège University Hospital Center, the Russian Ministry of the Interior and Deutsche Bahn.
We do not know exactly who is behind Wannacry, but the person who managed to stop his spread is Marcus Hutchins.
The solution he found to stop the spread of the WannaCry ransomware was simple and he had found it by chance.
The ransomware was activated only if a specific domain name was not purchased: when he bought the domain name on behalf of the company Kryptos Logic, the malware was automatically turned off.
Zeus
The Zeus Trojan is a type of malicious program (malware) that targets Microsoft Windows and is often used to steal financial data. Originally detected in 2007, the Zeus Trojan, often called Zbot, has become one of the most efficient botnets in the world, infecting millions of machines and spawning many similar malicious programs developed from its code.
It first creates a botnet, which is a network of infected machines that are secretly controlled by a command and a control server that the owner of the malicious program manages. As we saw in the first part of this article, a botnet allows the owner to collect astronomical amounts of information or execute large-scale attacks.
Zeus also acts as a banking Trojan designed to steal banking login credentials on machines it infects by monitoring websites and recording keystrokes.
Some forms of this malicious program also affect mobile devices by attempting to bypass the two-factor authentication that is becoming widespread in the financial services sector.
It uses two main methods of infection:
- Junk mail (spam)
- Inadvertent download
Mirai
Mirai is malware that transforms computers using the Linux operating system into remote-controlled bots, forming a botnet (see beginning of the article) used in particular to carry out large-scale attacks on networks. It mainly targets consumer devices such as remote controllable cameras or routers for the home... (IOTs)
Mirai then identifies vulnerable IoT objects using a table of default IDs and passwords and then simply logs on to install the malware.
There are hundreds of thousands of devices connected to the Internetthat use default settings, which makes them vulnerable to this type of attack. Once infected, the device monitors a Command and Control (C & C) server that is used to indicate the target of an attack.
On October 21, 2016, several major DDoS attacks on Dyn DNS services were carried out using Mirai botnets, causing difficulties to access sites such as GitHub, Twitter, Reddit, Netflix, Airbnb and many others...
The source code for Mirai malware was released in late October 2016 on hacker forums and then on Github. Since this source code has been released, the same techniques have been adapted in other malware projects.
The author of Mirai will hide behind the pseudonym Anna-Senpai. I invite you to discover Bryan Krebs' article on this subject:
https://krebsonsecurity.com/2017/01/who-is-anna-senpai-the-mirai-worm-author/
Petya/NotPetya

If you thought it sounded like the WannaCry ransomware attack, you were right.
Petya is a ransomware for Windows systems: it makes unavailable data from a computer, which can only be unlocked by paying a ransom.
Just like Wannacry, the unknown attacker used a feat developed by the National Security Agency (NSA), EternalBlue, which leaked a few months earlier. The attacker installed the backdoor on thousands of computers, which was then used to deliver a ransomware payload.
Once installed on a computer, Petya will seek full authority and identify other devices on the same network.
The ransomware will then search the computer it has infected to recover identifiers and passwords that it will then be able to reuse in the network to take control of more devices and multiply its spread.
Then, using conventional Windows features used to manage networks, it will transfer to other machines.
Petya has clearly burdened the turnover of the flagship of the French industry Saint-Gobain, the French company hardest hit by this destructive software. The latter estimates that her infection cost her in the first half 220 million euros in sales and 65 million euros in operating income (4.4%).
I love you
This worm also bore the names Loveletter and The Love Bug. He was hiding a malicious VBS scriptfake love letter. This script allowed the spread of this worm through a massive spread through Outlook. It added keys in the registry allowing it to start every time Windows starts. It was inserted in the files * .JPG, * .JPEG, * .VBS, * .VBE, * .JS, * .JSE, * .CSS, * .WSH, * .SCT, * .DOC * .HTA and renamed them by adding .VBS
ILOVEYOU first infected the Philippines, then almost all of Asia, Europe, Africa and the Americas.
It spread over four days on more than 3.1 million machines worldwide
I love you infected 10% of computers connected to the Internet : approximately $ 5 billion in estimated damages.
Its authors were Filipinos, Irene and Onel de Guzman and Reomel Lamores.
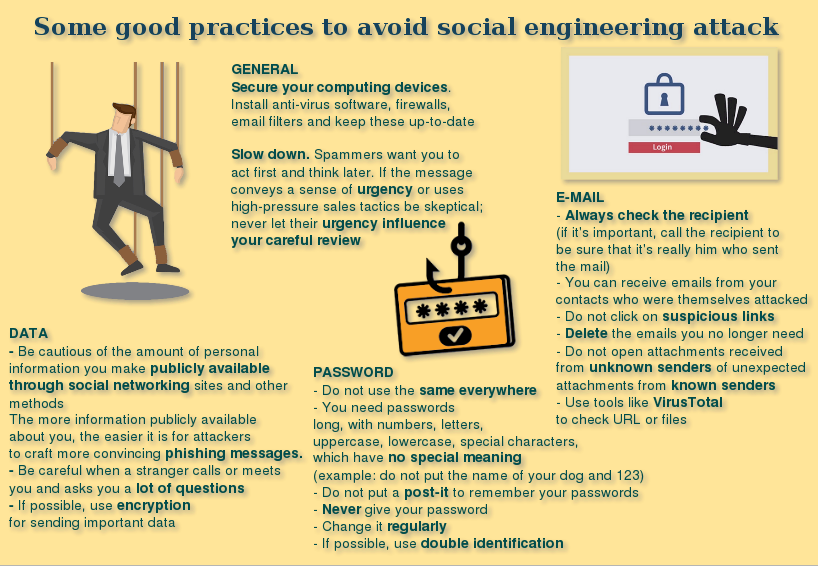
Some protective measures to take and how to detect an infection
Protection:
- Have an updated antivirus.
- Use Virustotal online tool to check files and websites.
- Do not record his passwords.
- Do not connect usb keys to strangers and friends (it can get infected).
- If you are on a network with other machines, and you notice an infection, disconnect from the network to avoid network contamination.
- Update systems as soon as there is a known security breach.
- Always check the extension of a file and the source of this file before opening it. Do not find unknown files
- Use double authentication
Sign of infection:
Programs today are so well done that they do not necessarily show signs of infection and are unobtrusive, but you can ask yourself questions if:
- The performance of your computer is reduced (long loading at startup and when launching programs, weird window that appear ...)
- You have a lot of ads, some opening themselves in a new tab
- If your mouse is moving by itself or if you can not do anything on your computer
Follow me on Twitter to be informed of my new articles/infographics →
 (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with