Index
Introduction

As we saw in my article on social engineering ( HERE), the first step of an attack is the information gathering, to know the target.
This can be any type of information: IP addresses, personal data, e-mails ...
We can generally summarize the different types of possible attacks in this way:
What is personal data?
Personal data is any information relating to a natural person identified or who can be identified, directly or indirectly, by reference to an identification number or to one or more elements that are specific to him.
Through this article, we will therefore study how information gathering is done, what tools are used to collect information and how to collect them.
Do not use these tools for malicious purposes without permissions (scanning an ip address if you do not have permission can be considered an attack).
This article is entirely dedicated to learning.
What is OSINT ?

Internet is an ocean of data, the information is easily accessible by all.
However some individuals can use this information by having malicious intentions (social engineering, phishing, threats, reselling information on the dark web ...)
There is a lot of data about you on the internet, whether it is data published directly by you (profiles on social networks, posts ...) or indirectly by someone around you.
OSINT or "Open Source Intelligence" is an intelligence method based on information accessible to all and not classified.
Open Source Intelligence is a fundamental element for intelligence operations.
OSINT uses all forms of publicly available sources, including:
Generally, the OSINT is done in 3 steps:
Tools for information gathering
Google Hacking
A Google Dork query is the use of search term that incorporates advanced search operators to find information on a website that is not available using a traditional search. This simplifies and clarifies searches.
Mainly used to obtain:
Here is a table that I realized that summarizes the most important operators to do advanced research:
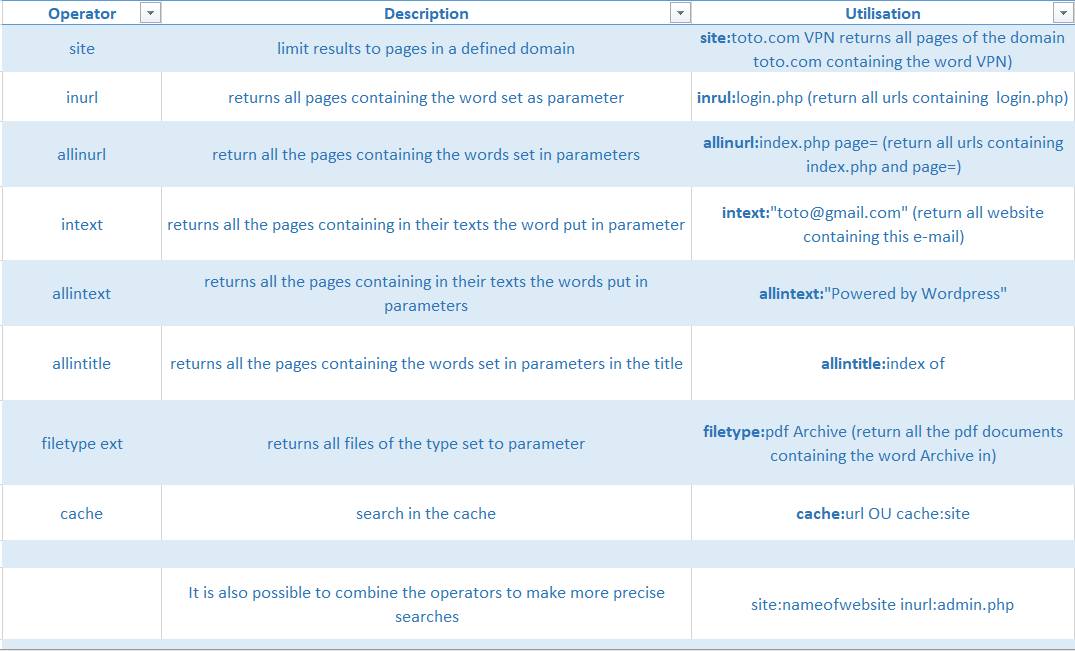
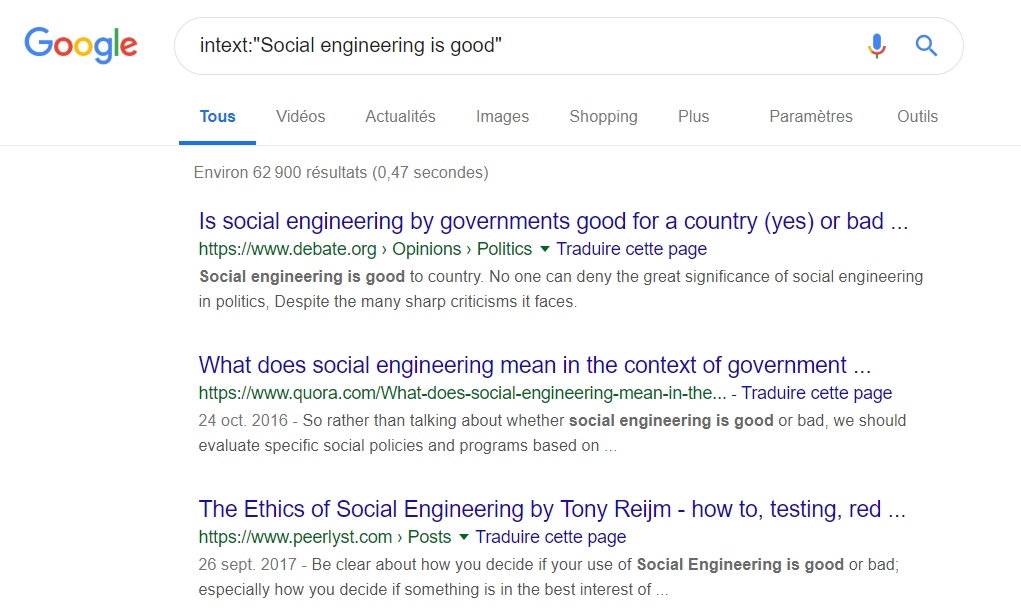
Example:
Shodan
https://www.shodan.io/
Shodan is a website specialized in finding objects connected to the Internet, and therefore having a visible IP address on the network. It allows to find a variety of web servers, routers as well as many devices such as printers or cameras.
For each result, we find the IP address of the server as well as other types of sensitive but accessible information.
Shodan is also a tool used by security researchers and hackers to search for poorly secured devices and take control of them with a single web browser.
Many devices use login / password combinations, often left by default, such as admin / admin or admin / 1234...
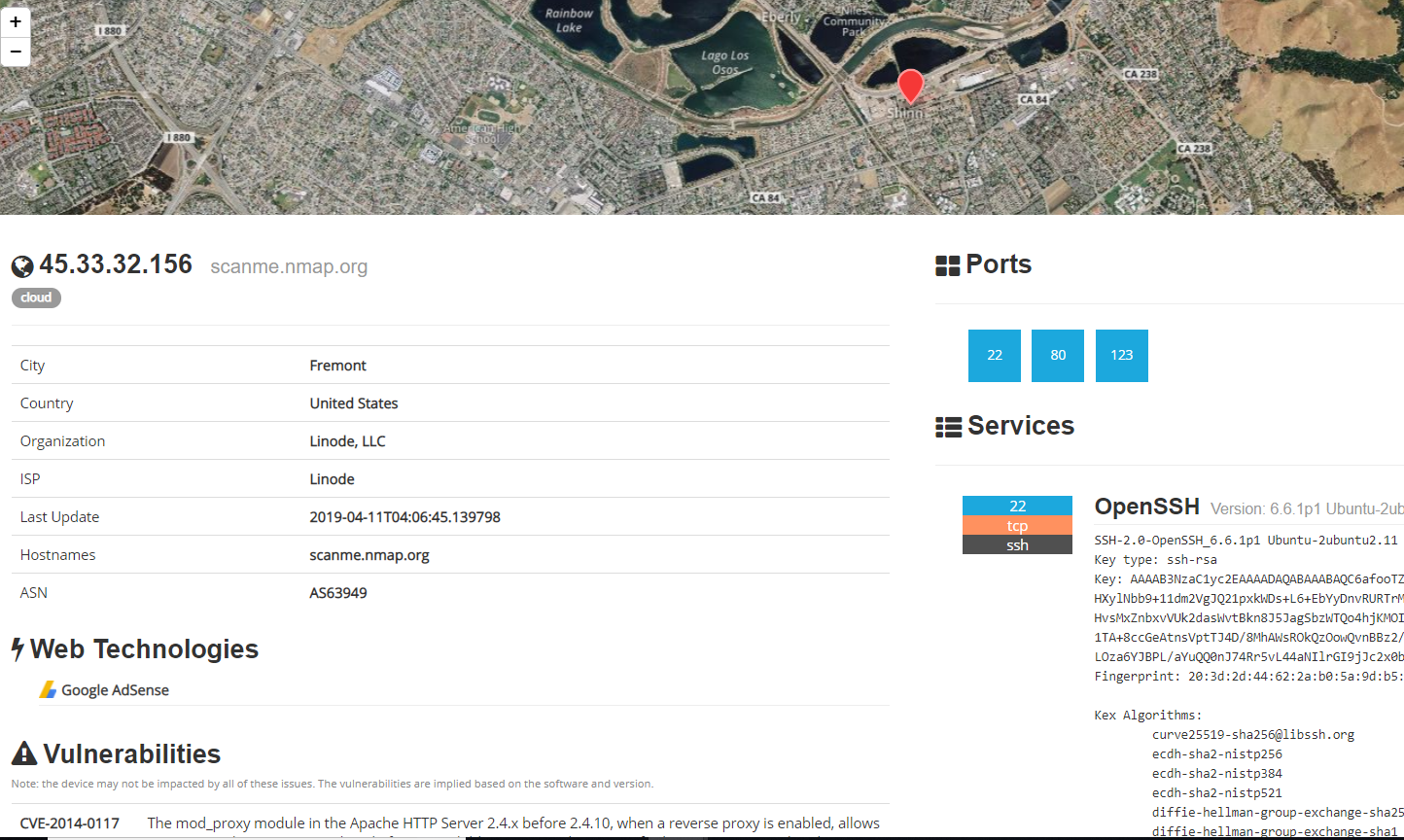
If I do a search in Shodan with the IP address 45.33.32.156 (this ip is provided by nmap to test our scans) here is some of the information I get:
Whois
Whois is a search service provided by Internet registries, for example Regional Internet Registries (RIR) or domain name registries to obtain information about an IP address or a domain name.
It allows:
This is the tool that will provide us with our first information.
This tool can be used both on the command line:
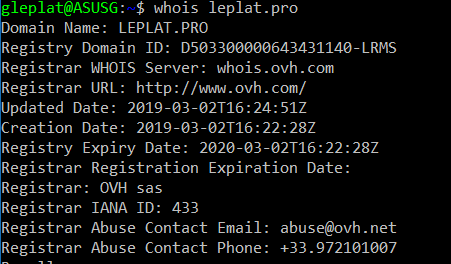
But also with GUI:
https://www.whois.com/whois/
The Harvester
The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
This tool is intended to help Penetration testers in the early stages of the penetration test in order to understand the customer footprint on the Internet.
It is also useful for anyone that wants to know what an attacker can see about their organization.
This is a complete rewrite of the tool with new features like:
Censys
Censys is a search engine (like Shodan) launched by researchers at the University of Michigan, which collects all the data it can on devices connected to IPv4 on the net. For this, it uses the ZMap open source port scanner and stores everything it retrieves in a database, which is then accessible via the web interface, an API or plain text listings to Download.
You can search by keywords, IP, domain name, protocol used, certificate ... etc. The information collected is also very comprehensive and can be used to identify potential security issues.
Example:
If I do a search in Censys with the IP address 45.33.32.156 (this ip is provided by nmap to test our scans) here is some of the information I get: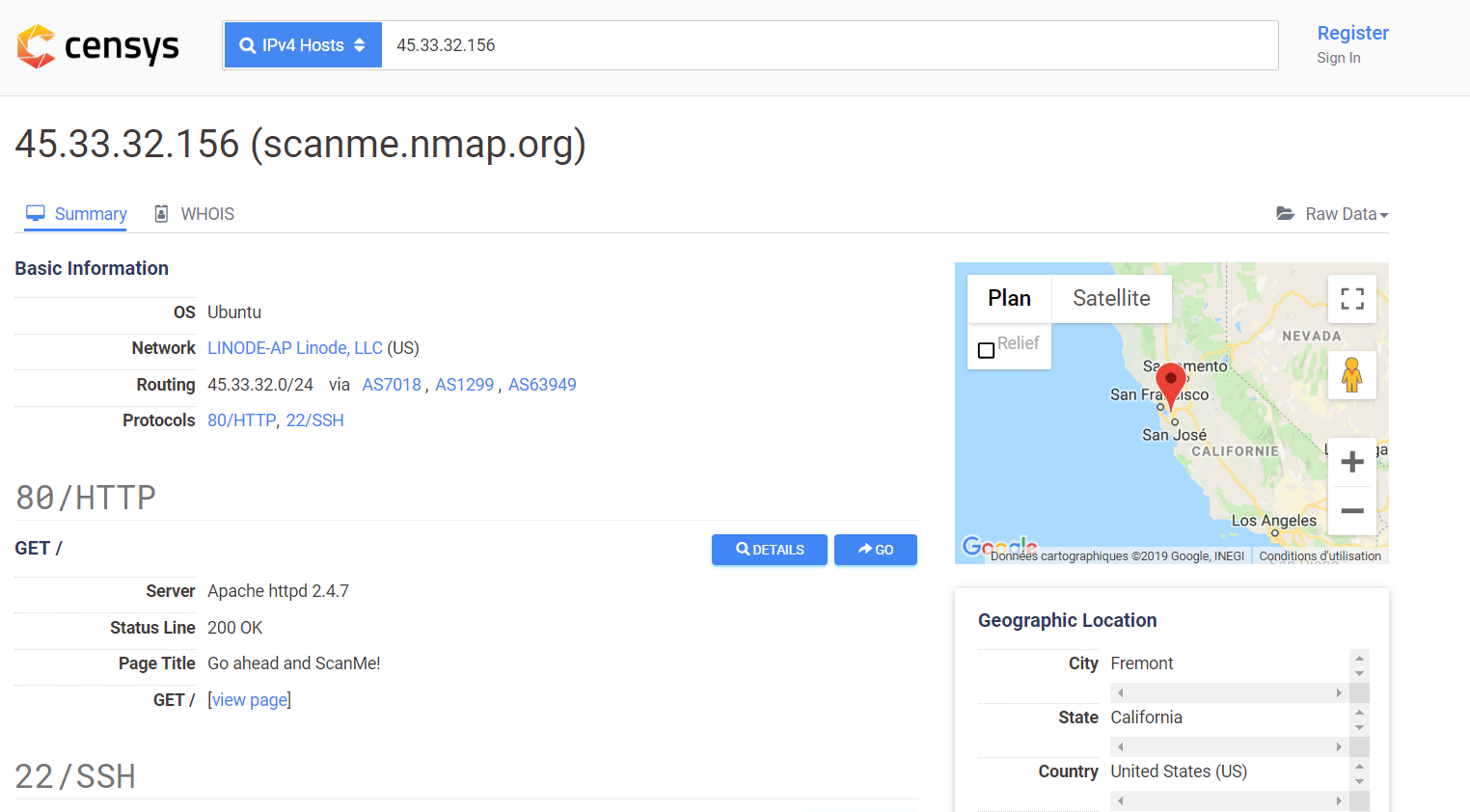
NMAP

Nmap is one of the most used tools in the world of security.
Is a free port scanner created by Fyodor and distributed by Insecure.org. It is designed to detect open ports, identify hosted services, and obtain information about the operating system of a remote computer.
To scan ports on a remote computer, Nmap uses a variety of scanning techniques that rely on protocols such as TCP, IP, UDP, or ICMP.
For more information on nmap, I made an article about this tool, do not hesitate to see: HERE
Maltego

Maltego is an open source software that allows to easily find, and visually, public information such as the different e-mail addresses of a person, phone numbers that may be associated with him, IP addresses, DNS, mail server, webhost, employees of a company and many other things.
SpiderFoot
https://www.spiderfoot.net/index.html
According to the official website of SpiderFoot:
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e-mail addresses, names and more. You simply specify the target you want to investigate, pick which modules to enable and then SpiderFoot will collect data to build up an understanding of all the entities and how they relate to each other.
Spiderfoot uses several different public sources such as Shodan, Google, SANS, Whois, PasteBin, etc. It is a cross platform tool, which works through any modern web browser.
The data returned from a SpiderFoot scan will reveal a lot of information about your target, providing insight into possible data leaks, vulnerabilities or other sensitive information that can be leveraged during a penetration test, red team exercise or for threat intelligence.
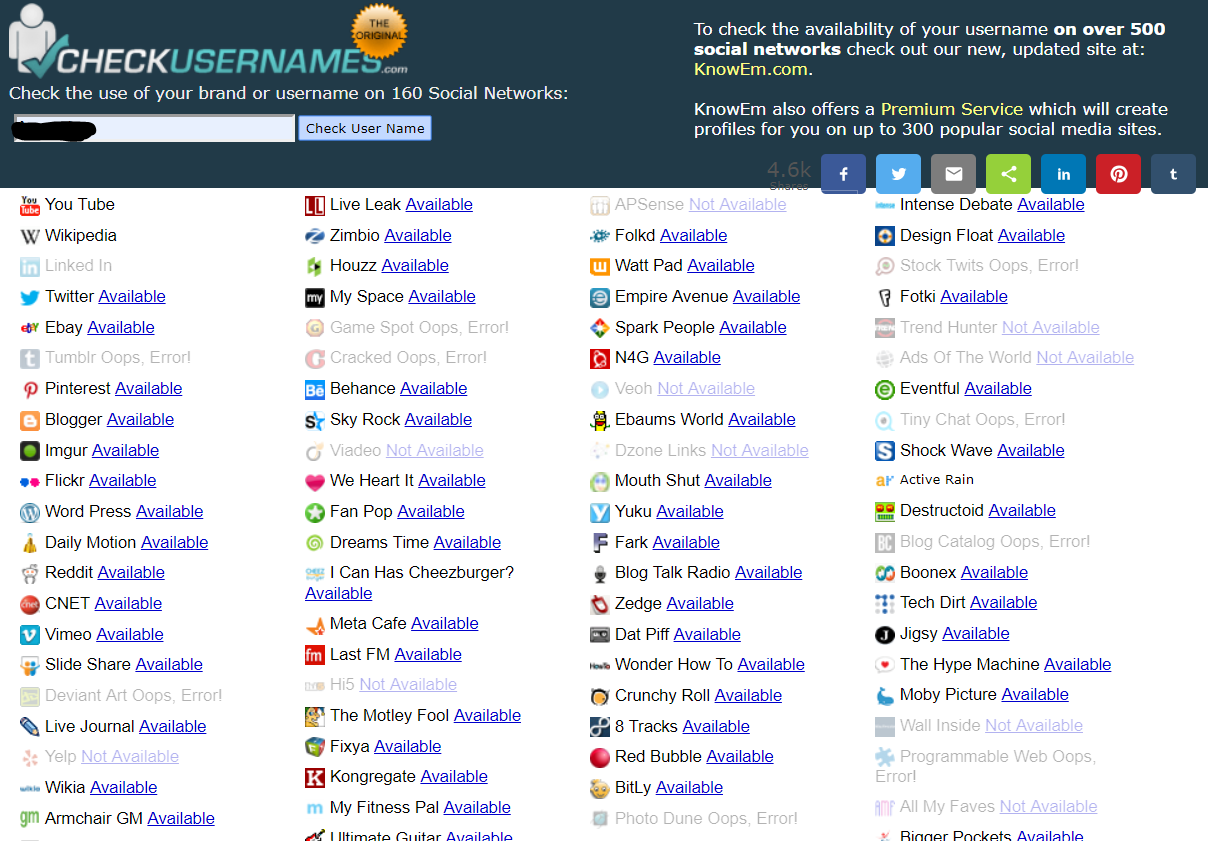
Checkusernames
https://checkusernames.com/
In the context of investigations or research of conventional information one may need to research if a person who is already known one of the nicks uses it on several social networks and online services.
This is a free service that can search in more than 160 social networks.
Just indicate the nickname already known for this service tells you all those on which it is still available. We will see that he is active for all the others and we will be able to visit them to verify that it is indeed the "target person".
Lullar
http://com.lullar.com/en

Conclusion
The Gathering information is the most important step in an attack, it can target potential flaws and define the attack vectors that attackers will use. The list of tools presented here is far from exhaustive, many tools are regularly released.
Thank you for reading my article, I hope it has been helpful.
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with
Buy me a coffee