Introduction
Many public and private actors are increasingly using contactless cards to identify their customers or users.
It raises the question of the interest of these cards about the security of the data they represent. This article dissect the use of these intermediaries representing us with a computer system. We can therefore focus on good practices and implementations vulnerable and avoid.
Index
- What is NFC ?
- Mifare
- Mifare Ultralight
- Mifare Classic
- Mifare DESFire
- Use on a coffee machine
- Conclusion


NFC
NFC, or Near Field Communication, is a technology for exchanging data between a reader and any compatible mobile terminal or between the terminals themselves. This is the technology your credit card uses for contactless payment, or your transport card. The advantage of this technology is that, in principle, no application is required. Just bring the two supports.
The NFC operates through a chip that allows the exchange of information between two devices equipped. This can be between 2 phones, between a phone and a terminal or a speaker. This technology is used by contactless card manufacturers. If your card is compatible, a small logo close to that of Wi-Fi is present on the latter.
NFC technology can make it easier to identify users, secure places (or not, we will see that), facilitate data transfer, facilitate payments, etc.
Mifare
Mifare is a registered trademark of NXP Semiconductors. MIFARE products are widely used integrated circuits for their use in the field of contactless smart cards and for many other applications around the world. The MIFARE range includes integrated circuits for contactless cards and readers for communicating with them. Mifare cards are used in many companies around the world.
Mifare Ultralight
MIFARE Ultralight cards are contactless cards intended to be used as a user identifier for a service. Its low cost makes it very accessible for many nascent companies wishing to modernize their service. The type of security present on the card depends on the category of the chosen card. Thus, several declensions are sold:
- Nano, without security
- EV 1, protected by a 32-bit password
- C, supporting the 3DES encryption
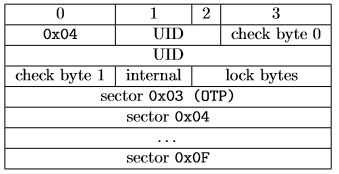
Byte 0 of the card has, according to the standard, the identifier of the manufacturer. For NXP this byte always takes the value 0x04. In addition, check bytes are used to check UID compliance and lock bytes are used to specify that some pages are read-only.
Security
As mentioned before, the MIFARE Ultralight Nano (when we talk about the MIFARE Ultralight, we generally refer to the MIFARE Ultralight Nano) has no security. This means that the memory is neither encrypted or signed. Exchanges with the reader are also neither encrypted or authenticated. There is only one verification of the non-alteration of exchanged data based on a CRC.Mifare Classic
MIFARE Classic cards are contactless cards for storing data. Indeed, these cards mainly contain a serial number and a data storage space whose size depends on the model:
- Classic 1k, offering 752 bytes of storage
- Classic 4k, offering about 4ko storage
The structure of the stored data is therefore the following:
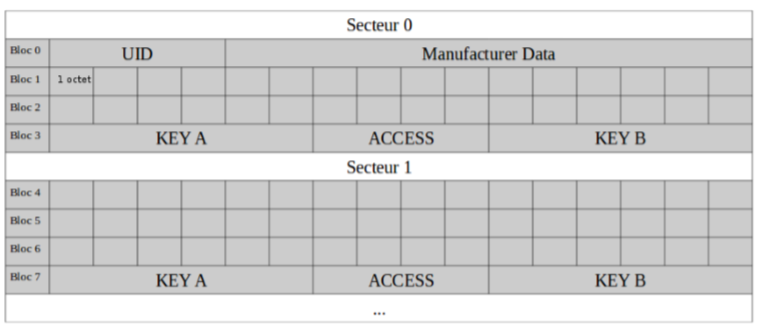
Thus the space is divided into sectors consisting of blocks of 16 bytes. The last block of each sector is used to store the 2 keys of the sector and the information related to the access to the sector. The number of sectors depends on the memory capacity of the product.
Management of memory access
A contactless card represents the identity of a person (an access badge, a customer card ...), or a right-hand pass (a pass for public transport, for access to a SPA. .). It is therefore necessary to ensure that it can not be copied. To copy a card, it would basically read all the data it has, and write them on a blank card. It is therefore in the interest of users to protect cards from fraudulent access. For this, NXP Semiconductors has implemented a memory access solutionbased on the use of two keys, called Key A and Key B.
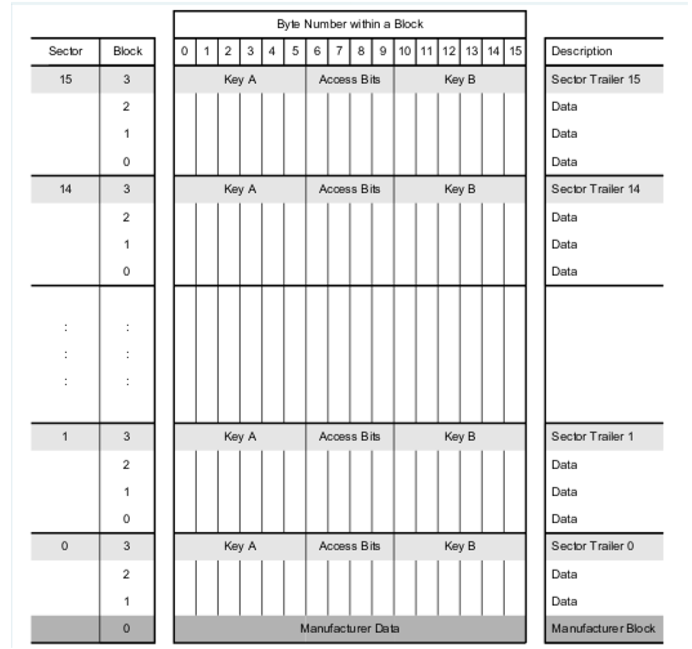
Using A and B keys
Each sector is composed of 4 blocks, including a block (the first in descending order) which is called the trailer block.
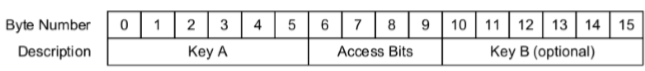
As shown in the table, the trailer block consists of three sections:
- The Key A, 6 bytes
- The sector access rule, called Access Bits, on 4 bytes
- The Key B, 6 bytes The section
- Define the reading and writing rights for each block independently
- Define the use of keys
- Limit the reading and writing of the trailer block
For example, it is possible to de fi ne the following things:
- Write access to block 0 is done by authenticating to the sector with the Key A
- Read and write access to block 1 and 2 is done by authenticating to the sector with the Key B
- Reading Key B is done by authenticating to the sector with Key A
NB: Key A can never be read, contrary to Key B, but can be written. The Access Bits section is divided into two parts, which are the same, but reversed. After much research, we have not found the reason for this specificity, so we think this is a way to validate the correct format of the desired access policies: indeed, some bit combinations do not are not possible.
Encryption of memory and exchanges
Recall the main purpose of the user: access to memory must be protected.
It's the case here, as we have seen with the trailer block and its Access Bits section.
In addition, we have seen that the MIFARE Classic embeds a cryptographic primitive used in the memory encryption and authentication during the exchange, called Crypto-1.
It is based on an LFSR (Linear Feedback Shift Register). The algorithm relies on 3 functions to generate random bits, but these functions are biased (according to a statistical study), which allows the construction of a distinction and the prediction of the number of turns made by the LFSR.
Two offline attacks
We define an off-line attack as an attack where we will not intercept the exchanges between a reader and a card. We will only rely on the values sent by the card and / or by the reader.The first attack is called the Nested Attack, and specifically targets the LFSR. This attack makes it possible to find the Key A and Key B of all the sectors if one knows at least one of any sector. It is based on the timing of the LFSR which makes it possible to calculate the number of laps performed and to find a value, assumed to be random, essential to authenticity on a sector.
The second attack is called the Keystream recovery Attack, and allows the recovery of a Key A or Key B. This attack is based on a weakness in the PRNG (Pseudo Random Number Generator) which deals with generating nuncios (sequence of bits random) and an interference on the part of the manufacturer concerning a response encrypted using the keystream whose clear is known: the value returned encrypted allows to recover 4 bits of the keystream.
In practice, if you want to find all the Key A / Key B couples, you have to proceed in several steps:
- If you know at least one key, then you use the Nested Attack directly
- If you do not know any key, we use the Keystream recovery Attack to recover one, then we use the Nested Attack which allows to find the others in record time
In real world
When a customer orders a batch of MIFARE Classic cards, the cards are pre-configured by default with the following key: 0xffffffffffff. If he does not think of changing it, he is then exposed to fraudulent access and illegal copying.
Note: If you plan to use MIFARE Classic 1K / 4K - which is no longer recommended at this time, be sure to modify all the keys so that you are not vulnerable to the Nested Attack. Indeed, the Keystream recovery attack is much longer to apply.
We saw uses of MIFARE Classic where a sector was always configured with the default keys, which allowed us to find all the other keys in less than a minute.
Mifare DESFire
MIFARE DESFire cards are contactless cards focused on the security of
stored data. For this, an operating system is implemented and manages access to
data in memory. Indeed, the storage space is not directly accessible and requires a
formatting that creates "application" memory spaces. These spaces correspond to the
user data.
3 versions of this model are on the market:
- Light: created to implement a single application
- EV1: limited to 28 applications containing a maximum of 32 files per application. The file size is fixed for each application when it is created
- EV2: which works in the same way as EV1 but can contain a number any application. The only limit is the memory on the card
Security
Compared with other models, this time security is at the heart of the implementation of these cards. Indeed, the data encryption can be ensured thanks to DES algorithms, 3DES or AES that are implemented in a hardware way. On AES versions, security options can be added as the possibility of using CMAC (Cypher-based Message Authentication Code).In addition, a mechanism anti-pulling card ensures that the transaction has been well when in communication with a reader.
Use on a coffee machine

Many machines are turning to a rechargeable card payment solution.
Indeed, it avoids having to store money in the machine, the problems of rendering the
currency and the user no longer has to have money on him to buy a coffee.
Offline
In the interests of ease of implementation and costs, we can find machines that do not are not connected to any network: they are independent.Description
To pay for a coffee on such a machine, just show the card after reloading it sufficient amount. The transaction is then carried out locally on the machine:- Reading the remaining amount
- If the credit is sufficient write the new credit on the card
So, this process can be done legitimately by the coffee machine, but also by any what other device to read / write such a card. That's why anyone is capable to modify the amount written on this card more or less easily.
Technical Underlying
To use a card payment on such a machine, this card must store all information necessary for payment, namely the amount remaining to which the user can access.
In addition, it must be legible and re-writable in order to modify the information after the transaction. We will see the uses usually made through two types of cards that we have studied.
Ultralight Nano
The first possibility is to use the Ultralight Nano cards to store information given that the amount of information is generally limited to an identifier user and a remaining amount.However, these cards have no protection of stored items. It is therefore possible to see and modify all the data present in the same way that the legitimate machine the would. Thus, there is no difficulty in modifying the data except for the knowledge that can do it.
Indeed, to recover and modify the amount present on a coffee machine card, simply to proceed in 4 steps:
- Take the card with currency and recover all the information stored using an NFC reader
- Pay a coffee with the card
- Recover again all the information stored on the card and identify the differences with the previous capture
- Understand how this information has been modified and how it should be written the information you want to store
Classic 1k
The second possibility is to use Classic 1k cards to store this information.The advantage of using this card is the establishment of security for the stored data. Indeed, the CRYPTO1 algorithm is used for encrypting the data on the card. However, the machine being offline, the keys used usually are the default keys 0xffffffffffff.
This choice is usually made because there is no management or storage of keys to be implemented. It is still possible to use the card in this way correctly. For that, it would be necessary to modify all the keys present on the card and to store these keys in the memory of the machine. In this way, one avoids being vulnerable to the Nested Attack.
Connected
In more advanced uses and for infrastructures with more resources, it is possible to connect the machine to a server. We then have a connected architecture.
A major drawback is then added: the service depends on the connection between the server and the machine.
Description
Now that the machine is connected to a server, it is possible to store information on this one.To pay a coffee, the user passes his card which has been put into operation beforehand. This card then has an identifier corresponding to its owner. The machine communicates then with the server to retrieve the information related to the credit of the customer and then perform the transaction with the server.
Technical Underlying
Here the security is based on the machine-server communication and the uniqueness of the identifier. In the card being used as abstraction of a user from the machine, it is sufficient to have on the card an identifier that can not be falsified.For this purpose, the Ultralight Nano and Classic 1k cards have fixed UIDs that identify a card. It is then sufficient to associate a card by its UID to a user. The server can then find information, including credit, associated with the user and make the necessary verifications from the server. So there is minimal trust to the user.
Conclusion

However, this convenience can be altered by the security of the cards storing the information.
This is why it is crucial and depends a lot on how to use it. These cards do not have a real security so it is recommended to store a minimum information. It is therefore strongly discouraged to use cards MIFARE Classic 1k / 4k or Ultralight for security purposes because their own security is itself in default. The type DESFire card is then more appropriate.
Follow me on Twitter to be informed of my new articles/infographics →
 (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with