Index
- Introduction
- How does a ATM work ?
- How does the theft of money in ATMs using malware ?
- What is the CEN/XFS standard ?
- Integrity control tools
- Black Box Attack
- Network Attack
- Conclusion
Introduction
Today, millions of people around the world use ATMs daily to make cash withdrawals, deposit money or pay for various services.
ATMs were introduced into our lives in 1967 when the first ATM was launched at a branch of London's Barclays Bank.
However, users and banks do not pay much attention to the security of these distributors.

How does a ATM work ?
Almost all ATMs are computers that typically contain:
- An operating system (mostly Windows XP ...)
- AN user interface software
- An ATM modalities administration application
- Communication software with the treatment center which ensures the IT and technological aspect of the transaction.
- An antivirus
The ATM processor encrypts the user data, which are of course not stored on the ATM hard disk, but directly sent to the bank server for comparison.
Often, the engineers in charge of the maintenance of the ATMs think that if the device works, it is better not to touch it, in other words, they are not updated ...
As a result, some ATMs still contain the critical vulnerability MS08-067 that allows remote code execution.
How does the theft of money in ATMs using malware ?
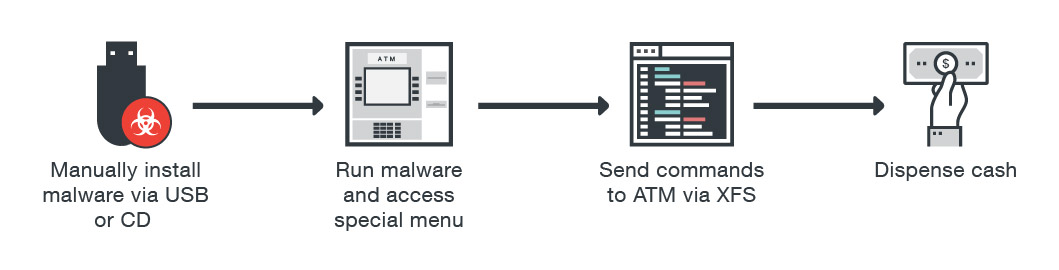
- 1 The malicious individual gets access, local or distant, to the distributor
- 2 The malicious code is injected into the ATMs system
- 3 In general, the infection is followed by the restart of the ATM. The system seems to restart in normal mode, but it is actually under the control of the malware, namely malicious individuals
- 4 The last step is the one that corresponds to the objective of the operation: the theft of money
What is the CEN/XFS standard ?
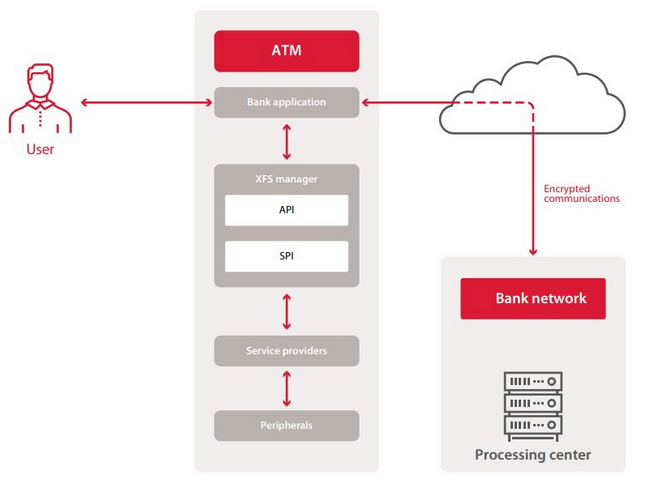
XFS (CEN / XFS, formerly WOSA / XFS) or eXtensions for Financial Services is a standard that provides a client-server architecture for the interaction of financial applications on a Windows platform with devices, including ATMs.
The purpose of this standard is to unify the operation of applications with any device, regardless of manufacturer, and offers a general API for this purpose.
This means that any application built with the XFS standard can administer low-level objects based solely on the logic described in this standard.
In resume, this is a standard for financial applications, but it does not provide for security.
This standard does not provide for authentication, and exclusive access to service providers is well implemented, but not for security reasons.
Integrity control tools
Some banks install applications on their ATMs to control the integrity. These promise to prevent the execution of unauthorized code on the basis of a whitelist, control external device and disk connections, and offer several other services that, theoretically, could be useful for resisting attacks.
Of course, these applications are not perfect and have vulnerabilities.
Often these vulnerabilities allow malicious individuals to access the operating system and perform their actions.
Black Box Attack
Two-thirds of the devices were also vulnerable to the "Black Box" attack, which consisted of directly connecting a mini-computer to the safe to order him to take out the money. This is possible because commands sent from the main application to the vault are neither encrypted nor authenticated. This attack nevertheless requires physical access to the vault connection interfaces.
- 1 The attacker opens the service area, he connects his black box to the ATM, which takes the place of the host and which bypasses all security measures implemented on the host such as antivirus software, tools integrity check, including full disk encryption, then closes the service area and leaves.
- 2 A little later, individuals who look like clients, approach ATM and withdraw money.
- 3 The attacker recover his black box.


Network Attack
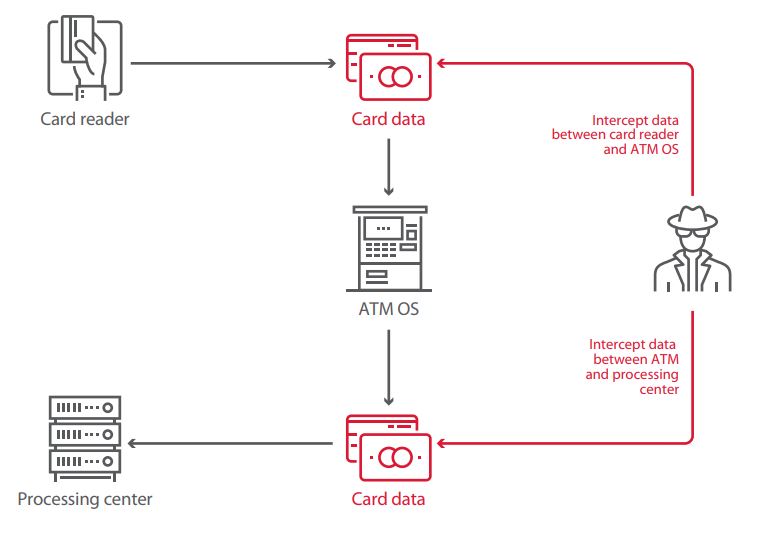
The connection between the ATMs and the treatment center can be protected in different ways. For example, using a software or hardware VPN, or through the implementation of SSL / TLS encryption, through the use of a firewall, or even MAC authentication implemented in xDC protocols . However, it seems that these measures sometimes seem so complicated for banks that none are applied.
This leaves the door open for man-in-the-middle attacks, where malicious individuals end up with banking data and all the money from ATM. Performing such attacks requires remote access to the device. To do this, simply use a vulnerable service accessible via the Internet.
A fake treatment center appears on the way to the authentic center. This false center then sends the ATM a money distribution order. And the money can be withdrawn using any card, even a card expired and with a zero balance. It is only necessary that this card is "recognized" by the false center.
Physical access to network hardware, including the ATM Ethernet cable, can also do the trick.
To find ATM vulnerable to this type of attack, attackers use search engines (you can read my article about OSINT --> HERE) like shodan.io
Conclusion
Jackpotting is back in fashion because ATMs are not really updated and the security of these systems leaves something to be desired.
Some safeguards should be taken to strengthen encryption, review the CEN / XFC standard, strengthen the physical hardware ...
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with
Buy me a coffee
